For years, the idea of a nation being digitally paralysed in a single, sweeping blow belonged to the realm of Hollywood thrillers. Films like Die Hard 4.0 turned cyber catastrophe into spectacle — a lone antagonist triggering blackouts, gridlock and financial collapse at the push of a button. At the time, such scenarios were dismissed as implausible, even alarmist, by security experts and policymakers who argued that modern states were simply too complex, too redundant and too resilient to fail all at once.Nearly two decades on, that confidence looks misplaced. As societies have wired power, payments, transport, communications and governance into a tightly interlinked digital ecosystem, the line between fiction and feasibility has blurred. Cyber intrusions, electronic warfare, satellite interference and information operations are no longer hypothetical future threats, but active tools of statecraft — used to probe, disrupt and coerce adversaries while staying below the threshold of open war.What cinema imagined as the plot of a single mastermind is today closer to a doctrine: a coordinated blend of cyber operations, electronic warfare and information manipulation designed to paralyse a society before the first shot is fired. From Eastern Europe to West Asia, modern conflicts show states increasingly seeking to disable opponents quietly, invisibly and persistently, reshaping the battlefield long before conventional force is applied.
This story asks a difficult “what if” question: what would a real Fire Sale look like today? How would such an assault unfold in the real world, which systems would be hit first, and how vulnerable would a digitally dependent country like India be if faced with a coordinated, multi-domain attack?
Fire Sale, demystified: From movie montage to real-world mechanics
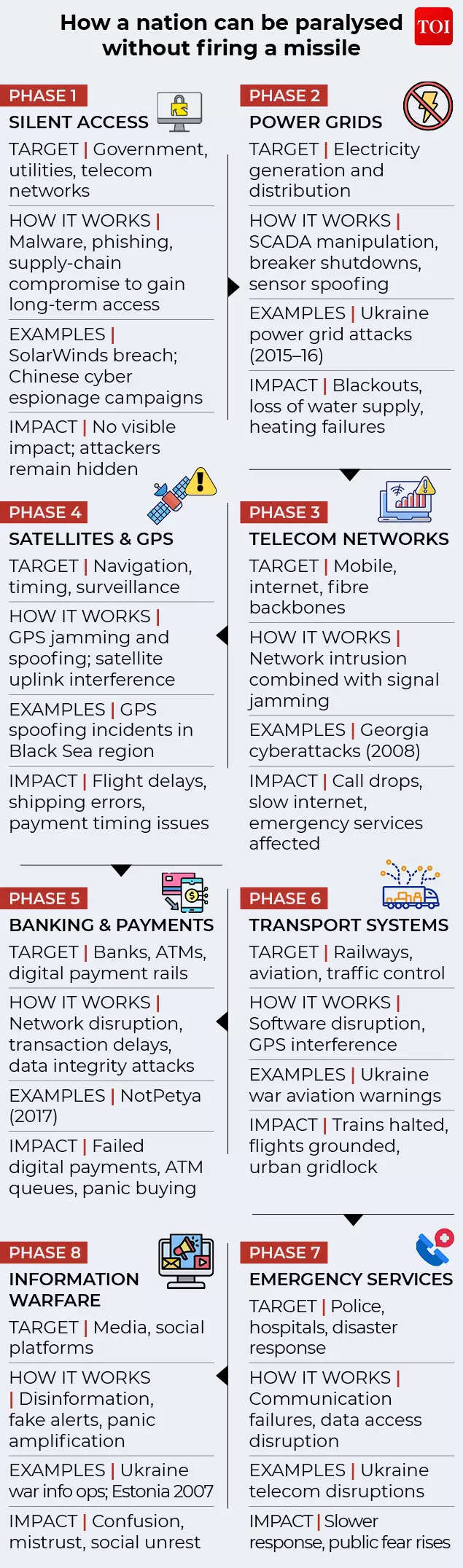
The genius — and the danger — of the Fire Sale concept lies not in a single spectacular hack, but in simultaneity. No modern nation collapses because one database is breached or one power station goes offline. Chaos emerges when multiple interdependent systems fail together, overwhelming the ability of authorities to respond.In fiction the sequence is compressed into cinematic minutes. In reality, a Fire Sale would likely unfold in phases, blending cyber intrusion, electronic disruption and psychological operations.
.
Phase one: Silent access and preparation
Long before any visible disruption, attackers would already be inside networks.This phase can take months or even years. Through phishing emails, compromised software updates, infected USB drives or supply-chain attacks, malicious code is implanted deep within critical systems. The goal is persistence, not noise — remaining undetected while mapping networks, stealing credentials and identifying choke points.The 2020 SolarWinds breach demonstrated how devastating this approach can be. By compromising a trusted software update, attackers gained access to thousands of government and corporate networks globally, many of which remained unaware for months.A modern Fire Sale would rely heavily on this kind of pre-positioning.
Phase two: Power grids — the backbone vulnerability
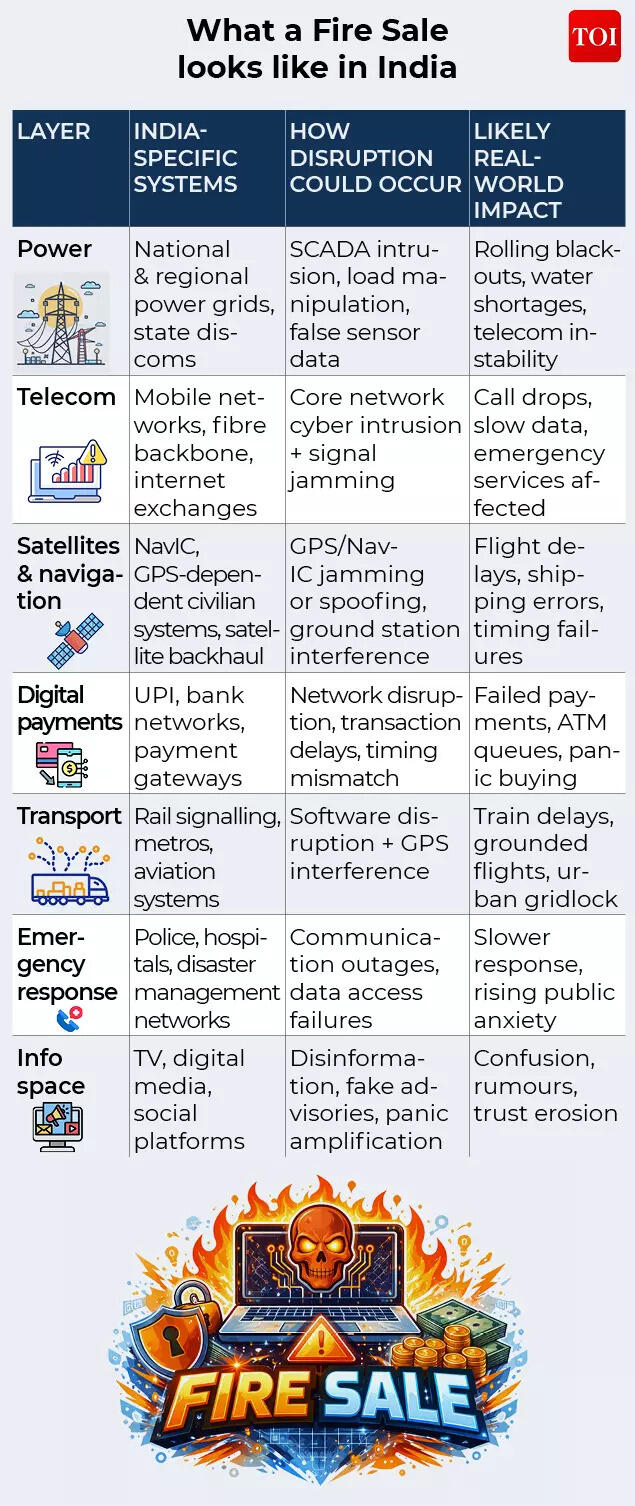
Electricity remains the foundation upon which almost all other systems rest.Power grids are especially vulnerable because they rely on industrial control systems (ICS) and supervisory control and data acquisition (SCADA) software, much of it designed decades ago with reliability — not security — in mind. Once inside, attackers can open breakers, damage turbines or manipulate sensor data so operators cannot see what is happening in real time.Ukraine’s power grid attacks in 2015 and 2016 offered a real-world preview. Hackers remotely отключed substations, leaving hundreds of thousands without electricity in the middle of winter. Crucially, they also targeted call centres, preventing customers from reporting outages — a detail that mirrors the Fire Sale’s emphasis on confusion.In India’s context, regional grids are interconnected. Disruption in one area can cascade rapidly, forcing emergency load shedding across states.

Phase three: Telecommunications and the fog of paralysis
If power is the backbone, telecommunications are the nervous system.Modern telecom networks — mobile towers, fibre backbones, internet exchanges — are tightly integrated with software-defined networking and centralised control. A coordinated cyber-EW assault could target:
- Core network switches
- Mobile network controllers
- Subsea cable landing stations
- Satellite-based backhaul links in remote areas
Electronic warfare adds another layer. By jamming or spoofing signals, attackers can degrade mobile connectivity even when physical infrastructure remains intact. During conflicts, GPS jamming has already caused civilian aircraft navigation warnings and shipping disruptions far from active battlefields.The result is not total blackout, but unreliability — calls dropping, data slowing, emergency services struggling to communicate. This grey-zone failure is often more damaging than a complete shutdown because it undermines trust.
Phase four: GPS, satellites and the invisible chokehold
Few civilian users realise how dependent daily life is on space-based systems.GPS is not just for navigation apps. It underpins:
- Power grid synchronisation
- Financial transaction timestamping
- Mobile network timing
- Aviation and maritime navigation
Electronic warfare units today routinely practice GPS jamming and spoofing — broadcasting false signals that mislead receivers rather than simply blocking them. In recent conflicts, vessels have reported being “teleported” dozens of kilometres inland by spoofed navigation data.Satellite interference does not require destroying satellites. Uplink and downlink jamming, cyber intrusion into ground stations, or dazzling sensors with directed energy can temporarily deny access — enough to disrupt operations during a crisis.For a Fire Sale scenario, this layer is critical: it disconnects systems from each other, even if they are internally functional.
Phase five: Banking, payments and financial confidence
Nothing triggers public panic faster than uncertainty over money.Modern banking systems are resilient in isolation, with redundancies and backups. Their vulnerability lies in interdependence — payment gateways rely on telecom networks, data centres depend on power, and interbank settlements require precise timing.A Fire Sale would not need to erase balances or loot accounts. Simply slowing or intermittently disrupting digital payments could be enough. Long queues at ATMs, failed UPI transactions, delayed salaries — these are psychological weapons as much as technical ones.The 2017 NotPetya malware showed how financial damage can ripple globally, causing billions of dollars in losses to companies that were not even the intended targets.
Phase six: Transport, traffic and emergency response
Air traffic control systems, railway signalling, metro operations and traffic management increasingly rely on networked software and GPS timing.Disruption here does not necessarily mean crashes — safety systems are designed to fail conservatively. Instead, the outcome is paralysis: grounded flights, halted trains, gridlocked cities.Emergency services face a double bind. As demand spikes due to outages and accidents, their ability to respond is degraded by the same network failures affecting everyone else.This is where a Fire Sale becomes socially destabilising rather than merely inconvenient.
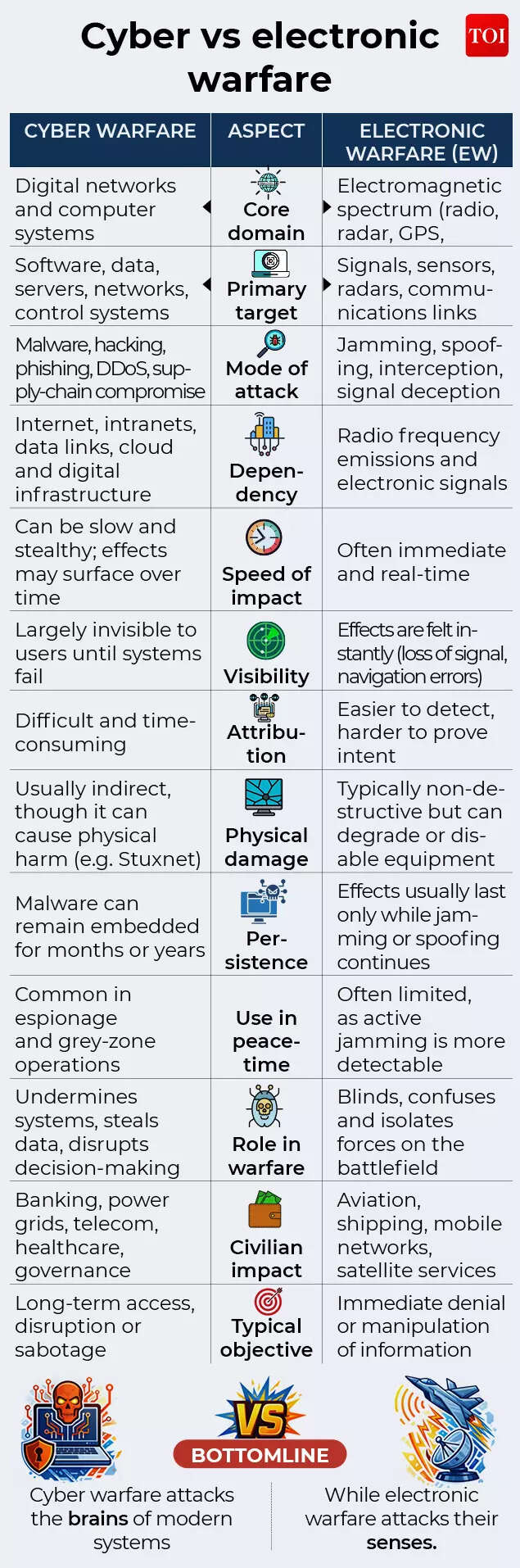
Cyber + electronic warfare: Why wars are now fought in the shadows
Cyber and electronic warfare have emerged as the quiet front lines of modern conflict, shaping outcomes long before the first missile is launched. Operating below the threshold of open war, these tools exploit the digital and electromagnetic foundations of contemporary societies, making them among the least visible — yet most potent — instruments of state power. Often described as a fifth domain alongside land, sea, air and space, cyber and EW enable states to weaken adversaries without crossing red lines that would trigger immediate military retaliation.Unlike conventional force, cyber and electronic attacks offer plausible deniability. Attribution is slow, technically complex and politically contested, allowing states to probe defences, signal intent or inflict damage while avoiding direct blame. This ambiguity has turned cyber and EW into preferred tools for coercion, escalation management and grey-zone warfare.
.
Modern military doctrine now tightly integrates cyber and electronic warfare with conventional operations. Before tanks advance or aircraft take off, adversary networks, sensors and data links are often targeted digitally to blind commanders and fracture decision-making. On the battlefield, GPS spoofing can distort navigation and targeting, while electronic jamming can sever units from command and control, reducing combat effectiveness without a single shot being fired.Crucially, civilian infrastructure is no longer a bystander. Power grids, telecom networks, satellites and digital payment systems increasingly form part of the battlespace, either because they directly support military operations or because disrupting them erodes public confidence and national resilience. In this shadowy domain, the objective is not immediate destruction, but sustained uncertainty — a form of warfare designed to exhaust, confuse and destabilise societies from within.
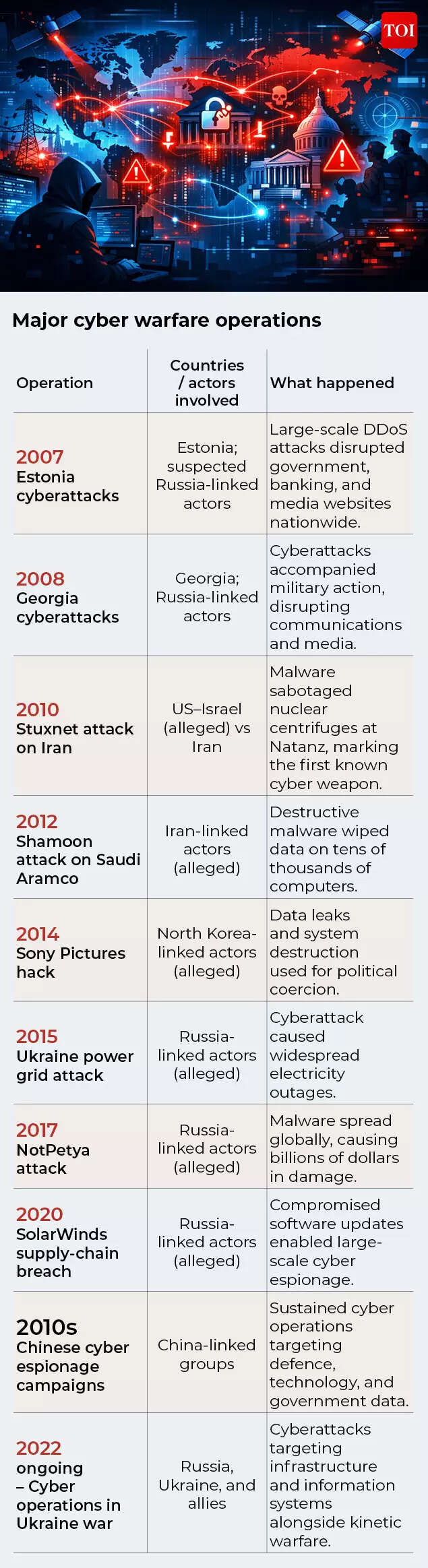
Real-world precedents: Fire Sales in fragments
While no country has yet experienced a full-spectrum “Fire Sale”, modern conflicts have repeatedly revealed its individual components in action. From the 2007 Estonia attacks that paralysed government and banking websites, to the Stuxnet malware that physically damaged Iran’s nuclear centrifuges, and from Ukraine’s power grid outages to the global fallout of the NotPetya attack, cyber operations have steadily expanded from disruption to destruction. The ongoing Ukraine war has taken this further, blending cyberattacks, satellite interference and information warfare alongside missiles and artillery. Taken together, these episodes show how reconnaissance, digital sabotage, escalation and deniability can be combined to destabilise states without a single, decisive blow — fragments of a Fire Sale that, if synchronised, could reshape modern warfare.
.
Each case illustrates a piece of the Fire Sale puzzle — reconnaissance, disruption, escalation and ambiguity.
Could India survive a Fire Sale?
India’s digital footprint has expanded at breathtaking speed. Power grids are smarter, payments are faster, governance is increasingly online. This brings efficiency — and exposure.India has taken institutional steps to address this reality. The formation of the Defence Cyber Agency marked formal recognition that future conflicts will involve sustained cyber operations targeting military networks, logistics chains and command systems. Parallel efforts in electronic warfare and space situational awareness reflect similar thinking.India’s strengths lie in scale and redundancy. Multiple grids, diverse telecom operators, and a mix of legacy and modern systems make total collapse difficult. Indigenous satellite navigation efforts aim to reduce dependence on foreign systems. Regular cyber exercises and red-team drills have improved awareness within critical sectors.Yet vulnerabilities remain.Civilian infrastructure is unevenly protected. State utilities, municipal systems and smaller contractors often lag behind central agencies in cyber hygiene. Supply-chain risks persist, especially where foreign hardware or software is involved. And as systems become more interconnected, the risk of cascading failure grows.A Fire Sale against India would not look like instant nationwide blackout. It would be messier, uneven — a patchwork of outages, delays and uncertainty that strains public trust and governance.



Leave a Reply